B.C.C MANAGEMENT AND BEKKER COMPLIANCE ARE PARTICIPATING
IN THE WORLD BUSINESS CONTINUITY AWARENESS WEEK.
Join us and book your place now for the webcast ” It wasn’t raining when Noah built the Ark!. Have a plan, be prepared!! “
B.C.C MANAGEMENT AND BEKKER COMPLIANCE ARE PARTICIPATING
IN THE WORLD BUSINESS CONTINUITY AWARENESS WEEK.
Join us and book your place now for the webcast ” It wasn’t raining when Noah built the Ark!. Have a plan, be prepared!! “
Technology alone will not solve the IT security problem.
Technology is an important part, but only a part of a comprehensive information security solution. Equally important is the development of an information security policy for your company, an assessment of your current situation, and training for all users and process owners.
Securing the internal network is as important as securing the external network (ex-employees, contractors, temporary personnel, fired employees, Viruses …)
Also never think that Security incidents won’t happen in your organization, no matter how big or small you are, because it does and once it hits it hits hard.
It is a must that the technical implementation is actually drafted from a policy not just on the ground only.
Security is part of an organization internal process never to be outsourced, Technical capabilities can be found outside but the process should be owned by the organization only.
Below are some 20 steps to consider for securing your Information Technology, Microsoft Windows Business environment:
One man do it all should not exist in your organization, small or big since it is a serious threat.
One man show was a phenomenon and is becoming more since the economy recession and this may lead to the organizations depending on one single person to do the Security/IT administration job and the High potential risk of losing him and its consequence on the job and security aspect. (Retirement, Firing, Resignation or Sudden Death)
Lock down your workstations and Network
Don’t Allow End Users and Administrators to Log On as Administrator
Create an alternative account non administrator for administrators, to do the daily work and when admin privileges is needed use the RunAs Feature, the application will run in administrator account privileges.
Disable Booting from CD, USB and everything else but the Primary Hard Disk, and put a password on the Bios.
With that in place no change can be done, or any trials of booting from alternative.
Rename the Administrator and Other Highly Privileged accounts, first thing a virus tries is to get admin privileges using the administrator account and trying passwords and if it is renamed with a strong password then it is 100 % Safe
Defeat Password Crackers Enable password complexity in your environment no matter what.
And enabled password lockout (be careful Viruses e.g.: Conficker.C) Disable LM hashing. And enable NTLM version 2 and run (LC 4 to test Cracking SAM)
Strengthen Windows Services.
Disable un-necessary service e.g. telephony or schedules.
Define the log on as a services accounts as a GPO.
Change Standard ports for Example SQL Server.
Work on NTFS permission for users files and important executable
And be careful on the registry it is an important part of security which you must secure, Firstly if it is possible to stop remote registry access, and always deny non admin user to have write on it.
Run Firewall, antivirus, spyware on local Workstation and on networks for example internet/email gateway (in case the antivirus on the Workstation is outdated or disabled) have different brands make sure you antivirus can’t be disabled or killed.
Separate the external network from the internal, using DMZ; never Ever publish any service directly to internet from the internal network.
Patch, Patch and Patch
Nothing more important as patching as an organization you need a patch management solution, there is plenty in the market for Example Windows SUS which comes for free.
Others such as SMS, GFI, Shavlik.
Get a remote access solution, in case there is a need for it or in case a disaster hit and no accessibility to the premises.
Get and Have an effective backup/Restore solution, Test Backups Frequently, and don’t forget to integrate it to the policy.
Disable FTP access to the outside world.
Invest in your network:
Get network firewalls (from layer 1 to layers 7 today’s viruses are on all layers) for VPN/IPSec Tunnels and segregation of network (VLANS)
Get web and email filters but an intrusion prevention system.
And not forgetting someone dedicated to look at the logs otherwise all the investment is thrown away
Also encrypt tunnels or data if you have more than one branch, never send clear data and never presume it is safe.
Lock, Log and protect the IT Server Room/Data Centre (theft, Fire, breaking, leakage)
Clustering Alone is not enough using Data replication where adequate also. Since Clustering only protects application failure not data.
Do periodic external checks using Nesuss or any other product just to see if you are exposed to the outside world.
Be careful of SNMP Components to change the password never leave them to defaults since a virus/technical person can issue command to shut them down or unauthorized access to the components can happen, which may lead to undesirable events.
Have all your employees acknowledge formally the IT/Security Policies and procedures.
Wireless:
Be careful from wireless Networks if they are configured wrongly.
Always have them behind a firewall; always use high encryption and never use static password connect them to a Radius server or any other password mechanism for ultimate security.
About BCCManagement:
We’ve been in Business since 2006, we have participated in several related International Conferences and seminars held in many countries including Canada, United Kingdom, and the United States.
Also, we published numerous Business Continuity studies and articles in renowned magazines and international websites, noting that BCCManagement had been actively involved in the development of standards dealing with Business Continuity namely the Business Continuity Standard BS25999.
In 2009 BCCManagement has done a corporate partnership with Business Continuity Institute BCI to Bring It’s Client the state of the art Business Continuity practice.
Posted in 27002-2005, bcc management, BCCMANAGEMENT, bccmanagement partnership bci, bccmanagement partnership with bci, BCCMANAGEMENT.COM, BCI, British Standards Institution, BS 25999, BS 25999-1:2006, BS 25999-2:2007, bs25999, BS25999-2:2007, BSI BS25999 CERTIFICATION PROCESS, I.t, iec 27002-2005, information security, iso 27002-2005, iso iec 27002-2005, it continuity, it security, middle east, Middle East and north africa, middle east north africa, securing Microsoft, securing Microsoft Windows, securing Microsoft Windows Business environment, securing Microsoft Windows environment, securing Windows
Tagged 20 steps for securing, BCCMANAGEMENT, BCCMANAGEMENT.COM, Business Continuity, Business Continuity Management, Business Continuity Planning, Business Impact Analysis, confiker, Contingency Planning, Continuity of Operations, IT Disaster Recovery, it security, Microsoft Windows Business environment, middle east, Operational Risk Management, Recovery Planning, Resiliency, Risk Assessment, securing it, securing Microsoft, securing Microsoft Windows, securing Microsoft Windows Business environment, securing Windows, securing your Information Technology, securing your IT, survey business continuity
BCCManagement.com Highlights the BSI BS25999 CERTIFICATION PROCESS
TAKING THE NEXT STEP:
ACCORDING TO BSI-GLOBAL
Initial Assessment
Stage 1
The following aspects will be covered:
Review of the organization’s BCMS documentation
High level evaluation of the organization’s readiness
Stage 2 assessment Review the organization’s understanding of the
requirements of the standard Understanding of the proposed scope of the stage 2 assessment
Review and confirm the resources needed for the stage 2 assessment
Plan the stage 2 assessment
Ensure that Management Reviews and audit/self assessments are being planned and performed Any areas deemed not in compliance will be raised as nonconformities and must be cleared and approved by the
lead auditor prior to moving into the Stage 2 phase of the
certification audit.
Stage 2
The purpose of the stage 2 audit is to evaluate the
implementation, including effectiveness, of the
organization’s BCMS.
This phase is carried out using the process audit approach.
Unlike a checklist approach, the audit approach assesses
all processes included in the scope of operation and all linked
processes to ensure effectiveness and consistency. This will
include interviews with the stakeholders, gathering of
objective evidence (procedures, reports and test results)
and evaluating those findings against the standard.
Any areas deemed not in compliance and/or effective will
be raised as nonconformities and must be cleared and
approved by the lead auditor prior to being recommended
for certification.
Surveillance Audit
The first surveillance visit is typically planned to take place
yearly after the date of the stage 2 audit.
BSI will perform periodic monitoring audits of the certified
organization’s BCMS. Typically, an organization may be
visited for such an audit once a year. The purpose of these
monitoring audits is to verify the certified organization’s
continued compliance with certification requirements.
Surveillance audits typically cover critical activities that ensure
continuous improvement and effectiveness such as:
Management review and audits/self assessments
Review of actions taken on nonconformities from previous audits
Effectiveness of the BCMS
Progress of planned activities aimed at continual improvement
Verifying the effective interaction among all BCMS elements
Continuing operational control
Review of any changes
Use of marks and any other reference to certification
Verifying a demonstrated commitment by the organization
to maintaining the BCMS effectiveness
Reassessment
The purpose of the reassessment audit is to confirm the
continued conformity and effectiveness of the BCMS and
its continued relevance and applicability for the scope of
certification. The reassessment audit will typically include
the following aspects:
The effectiveness of the BCMS in its entirety in the light of
internal and external changes and applicability to the
scope of certification.
Demonstrated commitment to maintain the effectiveness
and improvement of the BCMS in order to enhance overall
performance.
Whether the operation of the certified BCMS contributes to
the achievement of the organizations policy and objectives.
All steps noted are typical accepted practice based on ISO 17021
and subject to revision at anytime.
Any areas deemed not in
compliance and/or effective will
be raised as nonconformities and
must be cleared and approved by
the lead auditor prior to being
recommended for certification.
BSI Management Systems How to deploy BS 25999
CONCLUSIONS
BS 25999 establishes the processes, principles and
terminology to address business continuity and availability
risk. It also provides a comprehensive set of controls based on
industry leading practices that help organizations develop,
implement, maintain and mature business continuity
processes. The standard can be used as a framework so that
those organizations without a BCMS can efficiently establish
a workable program, and those that already have a program
can ensure it meets best practices where applicable.
The growing consensus regarding BS 25999, combined with
the opportunity to become certified in its use, provides
unparalleled benefits to companies of all sizes whose
customers rely on their products and services
Reference:
BSI Global
Posted in bcc management, BCCMANAGEMENT, bccmanagement partnership bci, bccmanagement partnership with bci, BCCMANAGEMENT.COM, BCI, bci partnership, British Standards Institution, BS 25999, BS 25999-1:2006, BS 25999-2:2007, bs25999, BS25999 CERTIFICATION PROCESS, BS25999-2:2007, BSI BS25999 CERTIFICATION PROCESS, BSI-GLOBAL, Business Continuity, Business Continuity Assessment, Business Continuity certification, Business Continuity certifications, Business Continuity Institute, Business Continuity Institutes, Business Continuity Management, business continuity middle east, business continuity mina, Business Continuity partnership, Business Continuity press realease, Business Continuity press release, business continuity strategy, business strategy, computer, continuity central, continuity planning, continuitycentral.com, Disaster Recovery, I.t, information security, it, it continuity, it security, mena, middle east, middle east north africa, network, networking, pandemic, partnership, press release, Security, swine flu, thebci.org, University, virus, Workforce Continuity
Tagged Availability Risk, Backup and Recovery, BCCMANAGEMENT, BCCMANAGEMENT.COM, BCM, BCP, BIA, BS 25999, bs 25999-1, BS 25999-1:2006, bs 25999-2, BS 25999-2:2007, bs25999, BS25999 CERTIFICATION PROCESS, BSI BS25999 CERTIFICATION PROCESS, BSI-GLOBAL, business, Business Continuity, Business Continuity Assessment, Business Continuity certifications, Business Continuity Management, Business Continuity Planning, Business Impact Analysis, Business Resiliency, confiker, Contingency Planning, Continuity of Operations, crisis, Crisis Management, Data Protection, Disaster Recovery, DSP, Dubai strategic plan, Emergency Notification, Emergency Preparedness, financial crisis, Incident Management, IT Disaster Recovery, it security, Mass Notification, middle east, Operational Risk Management, Recovery Planning, Recovery Plans, Resiliency, Risk Assessment, strategic plan, survey business continuity, virus, Workforce Continuity
Over the weekend, Mexico and the US had reported, Swine Flu Outbreak H1N1 in Human.
As of 06:00 GMT, 4 May 2009, 20 countries have officially reported 985 cases of influenza A (H1N1) infection.
Is your pandemic plan related to World Health Organization
WHO Alert Phase System?

Here are some questions to think about:
Do you have a plan?
Are you at least thinking of preparing?
Are you employees advised to use masks?
Are you plan ready and revised?
Be careful the layoffs revisit your plan and re-assign where gaps available
Does the plan include remote or working from home or reduction to 40 % operations?
Does your plan include remote teleconferencing capabilities?
Do you have an internal Communication plan for all employees to notify them of the status?
Does you plan include lowering visit of vendors to your premises to the minimal?
Does your plan include notifying your customers if you stop your business for a short term?
Key personnel affected and might not show up to work
Employees may choose to stay at home rather than risk exposure;
Offices closed (either someone sick or by the authorities);
The Supply chain may be affected;
Transport systems may be stoped;
Overwhelm of communication systems being exhausted that might affect your office and your remote users.
Customer not being serviced;
To view the latest Pandemic Map
Google Pandemic (2009 H1N1 Flu Outbreak Map)
http://swinemap.org
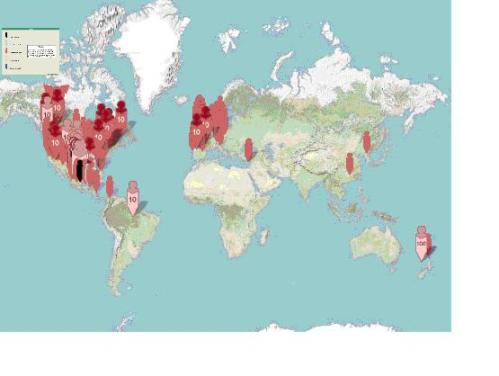 Courtesy of Google Maps (As of May 4 2009)
Courtesy of Google Maps (As of May 4 2009)
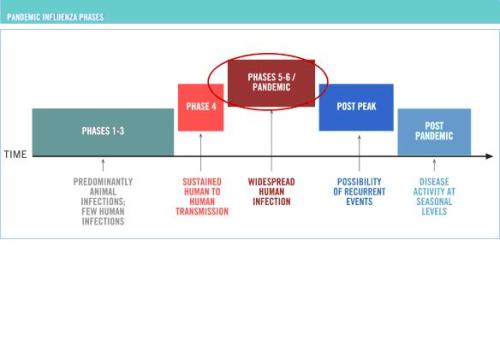 WHO Pandemic Phases
WHO Pandemic Phases
“There is one thing stronger than all the armies in the
world: and that is an idea/plan whose time has come.”
-Victor Hugo
References:
Use of masks WHO advise 3 may 2009
http://www.who.int/csr/resources/publications/Adviceusemaskscommunityrevised.pdf
List of infected countries
http://www.who.int/csr/don/2009_05_04/en/index.html
Google Maps
BCC management BCCManagement.com has been in business since 2006. It specializes in business continuity, disaster recovery planning, and strategic reviews of conceptual plans. www.BCCManagement.com
Posted in BCCMANAGEMENT, BCCMANAGEMENT.COM, Business Continuity, continuity planning, pandemic, Security, swine flu, virus, Workforce Continuity
Tagged Availability Risk, Backup and Recovery, BCCMANAGEMENT, BCCMANAGEMENT.COM, BCM, BCP, bird flu, bird flu h1n1, business contin, Business Continuity, business continuity consultancy, Business Continuity Management, Business Impact Analysis, Business Resiliency, Contingency Planning, Continuity of Operations, COOP, crisis, Crisis Management, Data Protection, Disaster Recovery, h1n1, Incident Management, Operational Risk Management, Pandemic Planning, Recovery Planning, Recovery Plans, Risk Assessment, strategic plan, swine flu, swine flu h1n1, virus, WHO, Workforce Continuity, World health organization